Silicon IP Cores
AES-CCM
AES-CCM Authenticated Encrypt/Decrypt Engine
The AES-CCM encryption IP core implements hardware Rijndael encoding and decoding in compliance with the NIST Advanced Encryption Standard. It processes 128-bit blocks, and is programmable for 128-, 192-, and 256-bit key lengths.
Two architectural versions are available to suit system requirements. The Standard version (AES-CCM-S) is more compact, using a 32-bit datapath and requiring 44/52/60 clock cycles for each data block (128/192/256-bit cipher key, respectively). The Fast version (AES-CCM-F) achieves higher throughput, using a 128-bit datapath and requiring 11/13/15 clock cycles for each data block.
CCM stands for Counter with CBC-MAC mode. CCM is a generic authenticate-and-encrypt block cipher mode. CBC-MAC is utilized to generate an authentication string while CTR mode is used to encrypt.
The AES-CCM core is a fully synchronous design and has been evaluated in a variety of technologies, and is available optimized for ASICs or FPGAs.
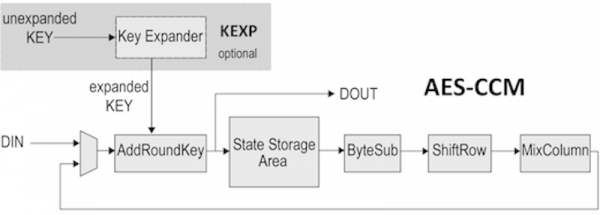
An AES encryption operation transforms a 128-bit block into a block of the same size. The encryption key can be chosen among three different sizes: 128, 192, or 256 bits. The key is expanded during cryptographic operations.
The AES algorithm consists of a series of steps repeated a number of times (rounds). The number of rounds depends on the size of the key and the data block. The intermediate cipher result is known as state. Initially, the incoming data and the key are added together in the AddRoundKey module. The result is stored in the State Storage area.
| KSIZE = 00 | KSIZE = 01 | KSIZE = 10 | |
|---|---|---|---|
| Rounds | 10 | 12 | 14 |
The state information is then retrieved and the ByteSub, Shiftrow, MixColumn and AddRoundKey functions are performed on it in the specified order. At the end of each round, the new state is stored in the State Storage area. These operations are repeated according to the number of rounds.
The final round is anomalous as the MixColumn step is skipped. The cipher is output after the final round.
CCM mode
During encryption, CBC-MAC is used to process the message data and additional data to produce an authentication value T. This is then encrypted using CTR mode. CTR mode is also used to encrypt the message. The output is an encrypted message and an encrypted authentication string U.
During decryption, the above steps are reversed. The message is decrypted first with CTR mode. The resulting decrypted message is processed, together with the additional data with CBC-MAC in order to produce the encrypted authentication string U. If the latter is different from the original U, the authentication has failed. In this case no other information (i.e. no decrypted data or the value of the authentication string) should be revealed except the failure itself.
Key Expansion
The AES algorithm requires an expanded key for encryption or decryption. The KEXP AES key expander core is available as an AES-CCM core option.
During encryption, the key expander can produce the expanded key on the fly while the AES core is consuming it. For decryption, though, the key must be pre-expanded and stored in an appropriate memory before being used by the AES core. This is because the core uses the expanded key backwards during decryption.
In some cases a key expander is not required. This might be the case when the key does not need to be changed (and so it can be stored in its expanded form) or when the key does not change very often (and thus it can be expanded more slowly in software).
The core has been verified through extensive synthesis, place and route and simulation runs. It has also been embedded in several products, and is proven both in ASIC and FPGA technologies.
Support
The core as delivered is warranted against defects for ninety days from purchase. Thirty days of phone and email technical support are included, starting with the first interaction. Additional maintenance and support options are available.
Deliverables
The core is available in ASIC (RTL) or FPGA (netlist) formats, and includes everything required for successful implementation. The ASIC version includes
- HDL RTL source
- Sophisticated HDL Testbench (self-checking)
- Simulation script, vectors & expected results
- Synthesis script
- User documentation
The AES-CCM can be mapped to any ASIC technology or FPGA device (provided sufficient silicon resources are available). The following are sample ASIC pre-layout results reported from synthesis with a silicon vendor design kit under typical conditions, with all core I/Os assumed to be routed on-chip. The provided figures do not represent the higher speed or smaller area for the core. Please contact CAST to get characterization data for your target configuration and technology.
AES-CCM Standard Core ASIC Implementation Results
|
ASIC Technology |
Number of eq. gates |
Freq (MHz) |
Throughput (Gbps) |
|---|---|---|---|
|
TSMC 7nm
|
7,328
|
1,700
|
4.94
|
|
TSMC 16nm
|
8,131
|
1,400
|
4.07
|
|
TSMC 28nm HPC |
10,097
|
1,300
|
3.78
|
Throughput for a 128-bit key size
AES-CCM Fast Core ASIC Implementation Results
|
ASIC Technology |
Number of eq. gates |
Freq (MHz) |
Throughput (Gbps) |
|---|---|---|---|
|
TSMC 7nm
|
19,279
|
1,000
|
11.63
|
|
TSMC 16nm
|
22,534
|
1,500
|
17.46
|
|
TSMC 28nm |
25.795
|
1,300
|
16.18
|
Throughput for a 128-bit key size
The AES-CCM can be mapped to any ASIC technology or FPGA device (provided sufficient silicon resources are available). The following are sample Altera FPGA results with all core I/Os assumed to be routed on-chip. The provided figures do not represent the higher speed or smaller area for the core. Please contact CAST to get characterization data for your target configuration and technology.
AES-CCM Standard Core
| Family | Logic Resources |
Memory Resources |
Freq. (MHz) |
Throughput (Mbps) |
|---|---|---|---|---|
| Arria 10 GX (-1) | 313 ALMs | 4 RAM Block | 300 | 873 |
| Stratix V (-1) | 312 ALMs | 4 RAM Block | 350 | 1,018 |
| MAX 10 (-7) | 547 LEs | 8 M9K | 110 | 320 |
Throughput for a 128-bit key size
AES-CCM Fast Core
| Family | Logic Resources |
Memory Resources |
Freq. (MHz) |
Throughput (Mbps) |
|---|---|---|---|---|
| Arria 10 GX (-1) | 858 ALMs | 16 RAM Block | 300 | 3,491 |
| Stratix V (-1) | 828 ALMs | 16 RAM Block | 320 | 3,724 |
| MAX 10 (-7) | 952 LEs | 32 M9K | 120 | 1,396 |
Throughput for a 128-bit key size
The AES-CCM can be mapped to any ASIC technology or FPGA device (provided sufficient silicon resources are available). The following are sample AMD FPGA results with all core I/Os assumed to be routed on-chip. The provided figures do not represent the higher speed or smaller area for the core. Please contact CAST to get characterization data for your target configuration and technology.
AES-CCM Standard Core
| Family (Speed Grade) | Logic Resources |
Memory Resources |
Freq (MHz) |
Throughput (Mbps) |
|---|---|---|---|---|
| Kintex-7 (-3) | 393 LUT | 2 BRAM | 300 | 873 |
| Kintex UltraScale (-3) | 390 LUT | 2 BRAM | 400 | 1,164 |
| Kintex UltraScale+ (-3) | 390 LUT | 2 BRAM | 525 | 1,527 |
| Versal (-2) | 471 LUT | 2 BRAM | 400 | 1,164 |
Throughput for a 128-bit key size
AES-CCM Fast Core
| Family (Speed Grade) | Logic Resources |
Memory Resources |
Freq (MHz) |
Throughput (Mbps) |
|---|---|---|---|---|
| Kintex-7 (-3) | 649 LUT | 8 BRAM | 250 | 2,909 |
| Virtex-7 (-3) | 721 LUT | 8 BRAM | 274 | 3,200 |
| Kintex UltraScale (-3) | 667 LUT | 8 BRAM | 375 | 4,364 |
| Kintex UltraScale+ (-3) | 667 LUT | 8 BRAM | 475 | 5,527 |
| Versal (-2) | 724 LUT | 8 BRAM | 325 | 3,782 |
Throughput for a 128-bit key size
Engineered by Ocean Logic.
Features List
- Encrypts and decrypts using the AES Rijndael Block Cipher Algorithm
- Satisfies Federal Information Processing Standard (FIPS) Publication 197 from the US National Institute of Standards and Technology (NIST)
- Processes 128-bit data in 32-bit blocks
- Employs user-programmable key size of 128, 192, or 256 bits
- Two architectural versions:
- Standard is more compact: 32-bit data path size
Processes each 128-bit data block in 44/52/60 clock cycles for 128/192/256-bit cipher keys, respectively - Fast yields higher transmission rates: 128-bit data path
Processes each 128-bit block in 11/13/15 clock cycles for 128/192/256-bit cipher keys, respectively
- Standard is more compact: 32-bit data path size
- NIST-Validated
- Works with a pre-expended key or can integrate the optional key expansion function
- Simple, fully synchronous, reusable design
- Available as fully functional and synthesizable VHDL or Verilog, or as a netlist for popular programmable devices
Resources
FIPS 197, Advanced Encryption Standard (AES): download PDF
AES test suite: The Advanced Encryption Standard Algorithm Validation Suite (AESAVS): download PDF